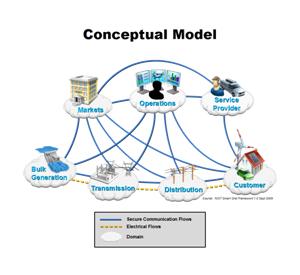
U117 Interface: Distribution SCADA and Distribution RTUs/IEDs
Logical Interface Characteristics
Categories 1-4:
Interface between control systems and equipment
- With or without high availability, and
- With or without compute and/or bandwidth constraints
|
Real-time data:
- power system status,
- measurements,
- settings, and
- control commands
|
Standards:
|
Cyber requirements::
- Availability = H
- Integrity = H
- Confidentiality = L
- Privacy = L
Cyber-Physical Requirements:
- Prevent attacks
- Deter / defer attacks
- Detect attacks
- Cope during attacks
- Recover from attacks
- Capture attack information
|
Cybersecurity Concerns & Failures:
- Denial of service
- Lost data
- Modified data
- Unvalidated data
- Late data
- Lack of data quality information
- Lack of alarms or event notifications
- Lack of alternate sources of critical information
- Invalid commands
|
Cyber-Physical Functional Policies, Procedures, and Technologies
The following table describes cyber-physical policies, procedures, and technologies that utilize power system functional and operational measures to mitigate the likelihood and impact of cyber attacks, while coping with any on-going attacks. The SG.XX-X items are references to the Smart Grid Catalog of Security
Requirements in the NISTIR 7628.
Functional Operational Policies
- Establish a communications architecture for SCADA operations that meets both functional and cyber requirements (SG.CM-1)
- Establish physically and/or logically separate networks for power system operations (SG.CM-1)
- Establish which types of personnel may have what types of access to SCADA systems and their applications (SG.PS-2)
- Establish role-based access control categories for personnel accessing SCADA systems and their applications (SG.AC-1)
- Establish role-based access control categories for personnel managing the information exchanges with Field Equipment (SG.AC-1)
- Establish access capabilities for each RBAC category based on “least privilege” concepts (SG.AC-7)
- Require adequate training of engineers on SCADA applications and information exchange systems with Field Equipment (SG.CP-1)
- Establish system, application, and information exchange testing policies (??)
- Establish system, application, and information exchange maintenance (SG.MA-1) and upgrade policies (SG.MA-2)
- Establish incident response policy between the utility and the Field Equipment (SG.IR-1)
- Develop policies for alternate or manual methods for var support if the SCADA applications or Field Equipment fail (SG.CP-1) (SG.SI-1)
|
Functional Operational Procedures
- Perform complete factory and field testing of SCADA applications and Field Equipment information exchange implementations
- Require trained engineers and SCADA applications to assess the reasonableness of information exchanged with Field Equipment
- Require validation of information exchanges between SCADA and Field Equipment
- Ensure adequate time accuracy, synchronization of systems, and update frequency for all systems
- Require periodic assessment of the accuracy of the SCADA application results
- Periodically require alternate or manual methods for data assessment to ensure user familiarity and adequacy of the results
- Develop SCADA system and application patching, maintenance, and upgrade procedures
- Ensure backup sources for critical systems and data
- Ensure that Field Equipment has default settings in cases of failed communications or failed associated equipment
- Ensure that communication failures are detected at all OSI layers, with appropriate notifications and resulting actions
|
Functional Operational Technologies
- Validate the reasonability of data and settings to be exchanged between the SCADA and Field Equipment
- Compare data against baseline settings to detect missing or inconsistent data
- Notify appropriate users if Field Equipment do not receive necessary or valid input, cannot respond correctly to the information exchange, or fail
- Implement a validation process to trigger notifications on possible unreasonable or extreme SCADA var requests for Field Equipment
- Implement IEC 61850 over DNPs with IEC 62351-5 security between the SCADA and Field Equipment
- Log and timestamp significant application events
- Log and timestamp each SCADA request for vars from Field Equipment
- Log and timestamp each Field Equipment response to var requests
- Log any system, application, and information exchange errors and failures
|
Cybersecurity Policies, Procedures, and Technologies
The following table describes the cybersecurity policies, procedures, and technologies that could mitigate the likelihood and impact of cyber attacks.
Cybersecurity Policies
- Require assurance from Field Equipment that they have established adequate security policies (and vice versa) (SG.SA-2)
- Establish supply chain policy between the utility and Field Equipment to ensure security of services (SG.SA-11)
- Perform a risk assessment on possible threats associated with interactions between the SCADA and the Field Equipment (SG.RA-4)
- Establish a security architecture for interactions between the SCADA and Field Equipment (SG.PM-4)
- Establish security policy requirement for authentication of information exchanged between the SCADA and Field Equipment (SG.IA-1)
- Establish role-based access control requirements including for interactions between the SCADA and Field Equipment (SG.AC-1)
- Establish cross-organization testing policies for procedures, systems, applications, and data exchanges (SG.SA-10)
- Establish audit and accountability policies and procedures between the utility and Field Equipment (SG.AU-1)
- Establish security awareness and training policies (SG.AT-1)
- Establish policy that all interactions between EMS and SCADA use isolated paths networks (SG.SC-2)
|
Cybersecurity Procedures
- Establish password requirements for personnel (SG.AC-21) (SG.IA-4)
- Establish strong (multifactor) authentication requirements for critical interactions (SG.IA-3)
- Establish certificate management requirements (SG.SC-1)
- Require timestamped login of all personnel accessing the EMS and SCADA systems (SG.AC-3) (SG.AU-8)
- Log all successful and unsuccessful logins (SG.AU-3)
- Establish procedures to detect multiple invalid login attempts and notify excessive failures (SG.AC-8)
- Establish and manage cryptographic keys, including revocation (SG.SC-11)
|
Cybersecurity Technologies
- Implement role-based access control (SG.AC-4)
- Implement a firewall between SCADA and Field Equipment systems (SG.AC-5)
- Ensure a trusted path is maintained at all times (SG.SC-10)
- Implement non-repudiation capabilities (SG.AU-16)
- Use validated cryptography (SG.SC-12)
- Implement intrusion detection and/or prevention systems (SG.SI-4)
|