3.8 Cyber Security Issues Affecting Distribution
3.8.1 Cyber Security Vulnerabilities and Attacks
The threats can be realized by many different types of attacks, some of which are illustrated in Figure 20. Often an attack takes advantage of a vulnerability, which may be due to human carelessness, an inadequately designed system, or circumstances such as a major storm. As can be seen, the same type of attack can often be involved in different security threats. This web of potential attacks means that there is not just one method of meeting a particular security requirement: each of the types of attacks that present a specific threat needs to be countered.
Although importance of specific cyber threats can vary greatly depending upon the assets being secured, some of the more common human and system vulnerabilities that enable attacks are:
- Lack of security: Security, even if it exists, is never “turned on”.
- Indiscretions by personnel: Employees write down their username and passwords and place them in their desk drawer.
- Simple or easy-to-guess passwords: Employees use short alpha-only passwords or use their dog’s name and/or their birthday as their password.
- Social engineering: An attacker uses personal information or subterfuge to learn a user’s password, such as pretending to be from a bank or leaning over someone’s shoulder as they type their password.
- Bypass controls: Employees turn off security measures, do not change default passwords, or everyone uses the same password to access all substation equipment. Or a software application is assumed to be in a secure environment, so does not authenticate its actions.
- Integrity violation: Data is modified without adequate validation, such that the modified data causes equipment to malfunction or allows access to unauthorized users or applications.
- Software updates and patches: The software is updated without adequate testing or validation such that worms, viruses, and Trojan Horses are allowed into otherwise secure systems. Alternatively, security patches needed to fix vulnerabilities are not applied.
- Lack of trust: Different organizations have different security requirements and use different cyber security standards.
Some common types of attacks include:
- Eavesdropping: a hacker “listens” to confidential or private data as it is transmitted, thus stealing the information. This is typically used to access intellectual property, market and financial data, personnel data, and other sensitive information.
- Masquerade: a hacker uses someone else’s credentials to pretend to be an authorized user, and thus able to steal information, take unauthorized actions, and possibly “plant” malware.
- Man-in-the-middle: a gateway, data server, communications channel, or other non-end equipment is compromised, so the data that is supposed to flow through this middle node is read or modified before it is sent on its way.
- Resource exhaustion: equipment is inadvertently (or deliberately) overloaded and cannot therefore perform its functions. Or a certificate expires and prevents access to equipment. This denial of service can seriously impact a power system operator trying to control the power system.
- Replay: a command being sent from one system to another is copied by an attacker. This command is then used at some other time to further the attacker’s purpose, such as tripping a breaker or limiting generation output.
- Trojan horse: the attacker adds malware to a system, possibly as part of an innocent-appearing enhancement or application, and possibly during the supply chain (e.g. during component manufacturing or system integration or shipping or during installation). This malware does nothing until some circumstance locally or remotely triggers it to cause an unauthorized action.
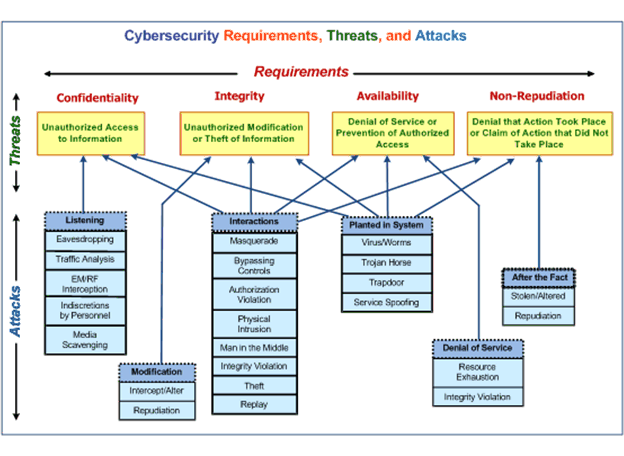
Figure 20 : Security Requirements, Threats, and Possible Attacks