Cybersecurity Concepts: Requirements, Threats, and Attacks
Cybersecurity Requirements, Threats, and Attacks
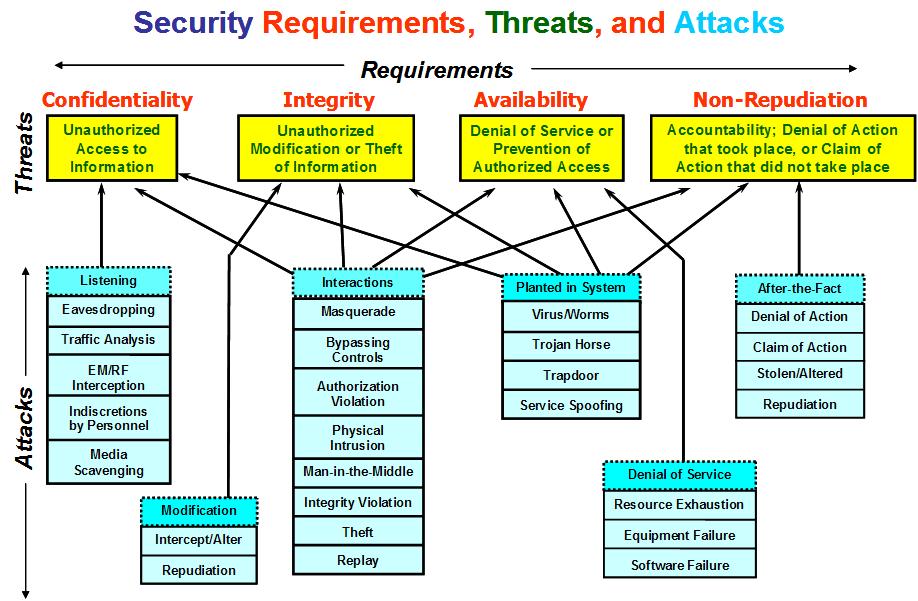
The following diagram illustrates some types cybersecurity attacks associated with the key threats to the security requirements of Confidentiality, Integrity, and Availability. Sometimes non-repudiation or accountability is added to this list.
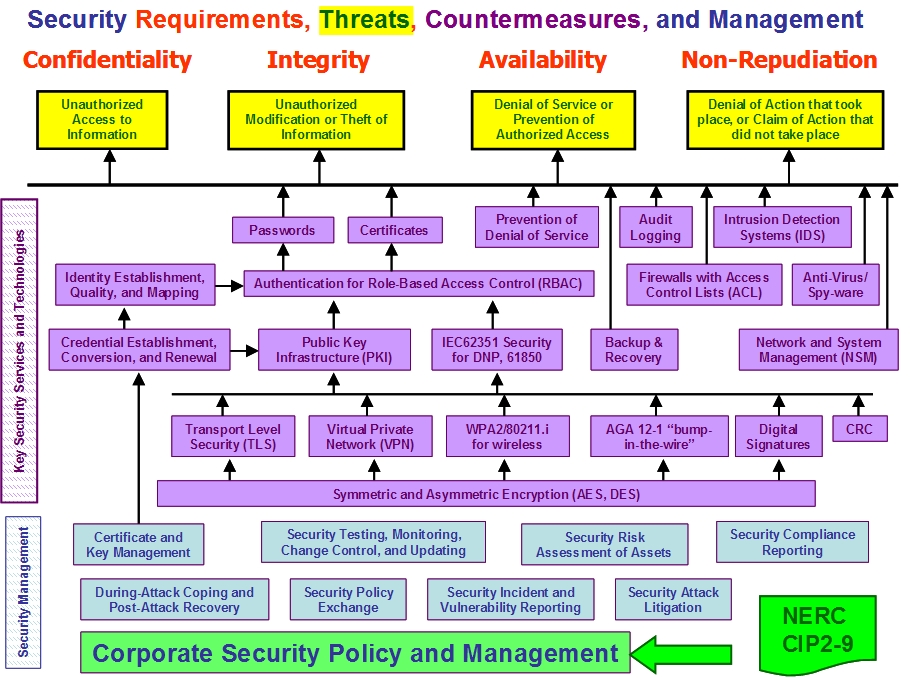
Cybersecurity Countermeasures
The following diagram illustrates just some of the methods for countering cyber threats.