|
Protection and securing of networked communications,
intelligent equipment, and the data and information that are vital to the
operation of the future energy system is one of the key drivers behind
developing an industry-level architecture. Cyber security faces
substantial challenges both institutional and technical. The IntelliGrid Architecture
documents serve to provide context to this complex topic as well as providing a
pathway by which the industry can work to develop a robust portfolio of
technologies to meet the critical issues that encompass security.
Security of the energy and communications systems
addressed by IntelliGrid Architecture faces multiple challenges from the following major trends:
-
Need for
greater levels of integration with a variety of business entities
-
Increased
use of open systems based infrastructures that will comprise the future
energy system
-
The need
for appropriate integration of existing or “legacy” systems with future systems
-
Growing
sophistication and complexity of integrated distributed computing systems
-
Growing
sophistication and threats from hostile communities
Security must be planned and designed into systems from
the start. Security functions are integral to the designs of systems.
Planning for security, in advance of deployment, will provide a more complete
and cost effective solution. Additionally, advanced planning will ensure
that security services are supportable (may be cost prohibitive to retrofit
into non-planned environments. This means that security needs to be
addressed at all levels of the architecture.
General Security
Process
 Security is a ever evolving process and is not
static. It takes continual work and education to help the security
processes keep up with the demands that will be placed on the systems.
Security will continue to be a race between corporate security
policies/security infrastructure and hostile entities. The security
processes and systems will continue to evolve in the future. By
definition there are no communication connected systems that are 100%
secure. There will be always be residual risks that must be taken into
account and managed. Security is a ever evolving process and is not
static. It takes continual work and education to help the security
processes keep up with the demands that will be placed on the systems.
Security will continue to be a race between corporate security
policies/security infrastructure and hostile entities. The security
processes and systems will continue to evolve in the future. By
definition there are no communication connected systems that are 100%
secure. There will be always be residual risks that must be taken into
account and managed.
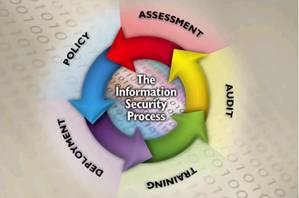
The normal thought process in regards to security.
It accurately reflects that the security process is a never-ending
process. Thus, in order to maintain security constant vigilance and monitoring
is needed as well as adaptation to changes in the overall environment. The
process depicts five (5) high level processes that are needed as part of a
robust security strategy. Although circular in nature, there is a
definite order to the process:
Security Assessment – Security assessment is the
process of assessing assets for their security requirements, based on probable
risks of attack, liability related to successful attacks, and costs for
ameliorating the risks and liabilities. The recommendations stemming from the
security requirements analysis leads to the creation of security policies, the
procurement of security-related products and services, and the implementation
of security procedures.
The implication of the circular process is that a security
re-assessment is required periodically. The re-evaluation period needs to
be prescribed for periodic review via policy. However, the policy needs to
continuously evaluate the technological and political changes that may require
immediate re-assessment.
Security Policy – Security policy generation is the
process of creating policies on managing, implementing, and deploying security
within a Security Domain. The recommendations produced by security assessment
are reviewed, and policies are developed to ensure that the security
recommendations are implemented and maintained over time.
Security Deployment – Security deployment is
a combination of purchasing and installing security products and services as
well as the implementation of the security policies and procedures developed
during the security policy process. As part of the deployment aspect of the
Security Policies, management procedures need to be implemented that allow
intrusion detection and audit capabilities, to name a few.
Security Training – Continuous training on security
threats, security technologies, corporate and legal policies that impact
security, Security measures analysis is a periodic,
and best practices is needed. It is this training in the security process
that will allow the security infrastructure to evolve.
Security Audit (Monitoring) – Security audit
is the process responsible for the detection of security attacks, detection of
security breaches, and the performance assessment of the installed security
infrastructure. However, the concept of an audit is typically applied to
post-event/incursion. The Security Domain model, as with active security
infrastructures, requires constant monitoring. Thus the audit process
needs to be enhanced.
When attempting to evaluate the security process on an
enterprise basis, as is required by IntelliGrid Architecture, it is impossible to account for all
of the business entities, politics, and technological choices that could be
chosen by the various entities that aggregate into the enterprise. Thus
to discuss security on an enterprise level is often a daunting task that may
never come to closure. In order to simplify the discussion, allow for
various entities to control their own resources, and to enable the discussion
to focus on the important aspects, security will be discussed in regards to
Security Domains.
|