|
|
IEC TC57 Security Standards for the Power System’s Information Infrastructure – Beyond Simple EncryptionBy Frances Cleveland, Xanthus Consulting International IEC TC57 WG15 Public Information
|
|
|
|
Figure 3: General Security Process – Continuous Cycle |
Security must be planned and designed into systems from the start. Security functions are integral to the designs of systems. Planning for security, in advance of deployment, will provide a more complete and cost effective solution. Additionally, advanced planning will ensure that security services are supportable (may be cost prohibitive to retrofit into non-planned environments. This means that security needs to be addressed at all levels of the architecture.
As shown in Figure 3, security is an ever evolving process and is not static. It takes continual work and education to help the security processes keep up with the demands that will be placed on the systems. Security will continue to be a race between corporate security policies/security infrastructure and hostile entities. The security processes and systems will continue to evolve in the future. By definition there are no communication connected systems that are 100% secure. There will be always be residual risks that must be taken into account and managed. Thus, in order to maintain security, constant vigilance and monitoring are needed as well as adaptation to changes in the overall environment.
The process depicts five high level processes that are needed as part of a robust security strategy. Although circular in nature, there is a definite order to the process:
Security Assessment – Security assessment is the process of assessing assets for their security requirements, based on probable risks of attack, liability related to successful attacks, and costs for ameliorating the risks and liabilities. The recommendations stemming from the security requirements analysis leads to the creation of security policies, the procurement of security-related products and services, and the implementation of security procedures.
The implication of the circular process is that a security re-assessment is required periodically. The re-evaluation period needs to be prescribed for periodic review via policy. However, the policy needs to continuously evaluate the technological and political changes that may require immediate re-assessment.
Security Policy – Security policy generation is the process of creating policies on managing, implementing, and deploying security within a Security Domain. The recommendations produced by security assessment are reviewed, and policies are developed to ensure that the security recommendations are implemented and maintained over time.
Security Deployment – Security deployment is a combination of purchasing and installing security products and services as well as the implementation of the security policies and procedures developed during the security policy process. As part of the deployment aspect of the Security Policies, management procedures need to be implemented that allow intrusion detection and audit capabilities, to name a few.
Security Training – Continuous training on security threats, security technologies, corporate and legal policies that impact security, Security measures analysis is a periodic, and best practices is needed. It is this training in the security process that will allow the security infrastructure to evolve.
Security Audit (Monitoring) – Security audit is the process responsible for the detection of security attacks, detection of security breaches, and the performance assessment of the installed security infrastructure. However, the concept of an audit is typically applied to post-event/incursion. The Security Domain model, as with active security infrastructures, requires constant monitoring. Thus the audit process needs to be enhanced.
When attempting to evaluate the security process on an enterprise basis, it is impossible to account for all of the business entities, politics, and technological choices that could be chosen by the various entities that aggregate into the enterprise. Thus to discuss security on an enterprise level is often a daunting task that may never come to closure. In order to simplify the discussion, allow for various entities to control their own resources, and to enable the discussion to focus on the important aspects, security will be discussed in regards to Security Domains.
Users, whether they are people or software applications, have zero or more of four basic security requirements, which protect them from four basic threats:
· Confidentiality – preventing the unauthorized access to information
· Integrity – preventing the unauthorized modification or theft of information
· Availability – preventing the denial of service and ensuring authorized access to information
· Non-Repudiation – preventing the denial of an action that took place or the claim of an action that did not take place.
The threats can be realized by many different types of attacks, some of which are illustrated in Figure 4. As can be seen, the same type of attack can often be involved in different security threats. This web of potential attacks means that there is not just one method of meeting a particular security requirement: each of the types of attacks that presents a specific threat needs to be countered.

Figure 4: Security Requirements, Threats, and Possible Attacks
Security countermeasures, as illustrated in Figure 5, are also a mesh of interrelated technologies and policies. Not all security countermeasures are needed or desired all of the time for all systems: this would be vast overkill and would tend to make the entire system unusable or very slow. Therefore, the first step is to identify which countermeasures are beneficial to meet which needs. These breakdowns are illustrated in Figure 6, Figure 7, Figure 8, and Figure 9.
In these figures, the four security requirements (confidentiality, integrity, availability, and non-repudiation) are shown in red words. The security threats are shown with a yellow background. The key security services and technologies used to counter the threats are shown in purple and tan, while security management items are shown in blue. Security policy is shown in green.
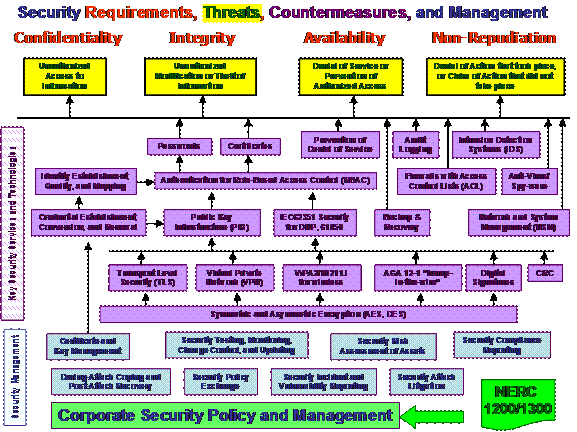
Figure 5: Overall Security: Security Requirements, Threats, Countermeasures, and Management
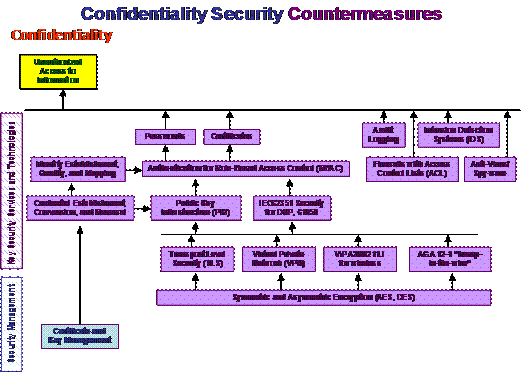
Figure 6: Confidentiality Security Countermeasures
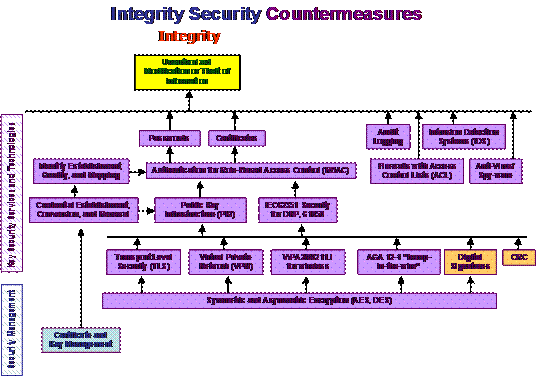
Figure 7: Integrity Security Countermeasures
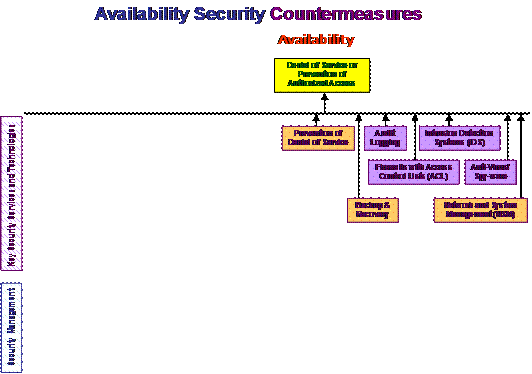
Figure 8: Availability Security Countermeasures
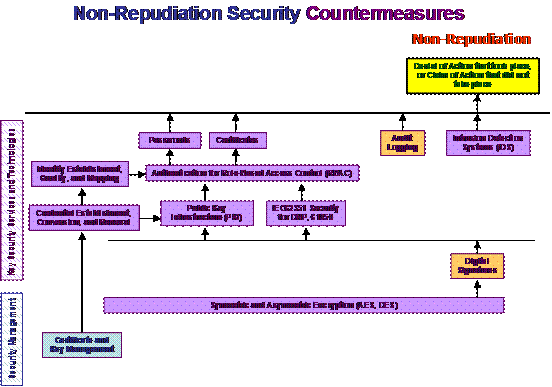
Figure 9: Non-Repudiation Security Countermeasures
Power system operations pose many security challenges that are different from most other industries. For instance, most security measures were developed to counter hackers on the Internet. The Internet environment is vastly different from the power system operations environment. Therefore, in the security industry there is typically a lack of understanding of the security requirements and the potential impact of security measures on the communication requirements of power system operations.
In particular, the security services and technologies have been developed primarily for industries that do not have many of the strict performance and reliability requirements that are needed by power system operations. For instance:
· Preventing an authorized dispatcher from accessing power system substation controls could have more serious consequences than preventing an authorized customer from accessing his banking account. Therefore, denial-of-service is far more important than in many typical Internet transactions.
· Many communication channels used in the power industry are narrowband, thus not permitting some of the overhead needed for certain security measures, such as encryption and key exchanges.
· Most systems and equipment are located in wide-spread, unmanned, remote sites with no access to the Internet. This makes key management and some other security measures difficult to implement.
· Many systems are connected by multi-drop communication channels, so normal network security measures cannot work.
· Although wireless communications are becoming widely used for many applications, utilities will need to be very careful where they implement these wireless technologies, partly because of the noisy electrical environment of substations, and partly because of the very rapid and extremely reliable response required by some applications.
Because of the large variety of communication methods and performance characteristics, as well as because no single security measure can counter all types of threats, it is expected than multiple layers of security measures will be implemented. For instance, VPNs only secure the transport level protocols, but do not secure the application level protocols, so that additional security measures, such as IEC 62351-4, provide the application level security, possibly running over VPNs. In addition, role-based access passwords, intrusion detection, access control lists, locked doors, and other security measures are necessary to provide additional levels of security.
It is clear from Figure 6 through Figure 9 that authentication plays a large role in many security measures. In fact, for most power system operations, authentication of control actions is far more important that “hiding” the data through encryption.
Also because connection to the Internet is (should not be) a factor, since power system operations should be well-protected by isolation and/or firewalls, some of the common threats are less critical, while others are more critical. Although importance of specific threats can vary greatly depending upon the assets being secured, some of the more critical threats are:
· Indiscretions by personnel – employees stick their passwords on their computer monitors or leave doors unlocked.
· Bypass controls – employees turn off security measures, do not change default passwords, or everyone uses the same password to access all substation equipment. Or a software application is assumed to be in a secure environment, so does not authenticate its actions.
· Authorization violation – someone undertakes actions for which they are not authorized, sometimes because of careless enforcement of authorization rules, or due to masquerade, theft, or other illegal means.
· Man-in-the-middle – a gateway, data server, communications channel, or other non-end equipment is compromised, so the data which is supposed to flow through this middle equipment is read or modified before it is sent on its way.
· Resource exhaustion – equipment is inadvertently (or deliberately) overloaded and cannot therefore perform its functions. Or a certificate expires and prevents access to equipment. This denial of service can seriously impact a power system operator trying to control the power system.
By 1997, IEC TC57 recognized that security would be necessary for these protocols. It therefore first established a temporary group (AdHoc WG06) to study the issues of security. This group published a Technical Report IEC 62210 on the security requirements. One of the recommendations of this Technical Report was to form a Working Group to develop security standards for the IEC TC57 protocols and their derivatives (i.e. DNP).
Therefore, IEC TC57 WG15 was formed in 1999, and has undertaken this work. The WG15 title is “Power system control and associated communications - Data and communication security” and its scope and purpose are to “Undertake the development of standards for security of the communication protocols defined by the IEC TC 57, specifically the IEC 60870-5 series, the IEC 60870-6 series, the IEC 61850 series, the IEC 61970 series, and the IEC 61968 series. Undertake the development of standards and/or technical reports on end-to-end security issues.”
The scope of the work of WG15 is to develop standards that increase the informational security assurance aspects of the protocols specified within TC57. As part of this work, concrete and implementable, standards are intended to be developed. These standards are intended to be specified, as needed, by utilities and implemented by responding vendors. WG15 is committed to develop relevant standards that increase the overall informational security assurance aspects of utility infrastructures.
The justification was that safety, security, and reliability have always been important issues in the design and operation of systems in the power industry, and cyber security is becoming increasingly important in this industry as it relies more and more on an information infrastructure. The deregulated market has imposed new threats as knowledge of assets of a competitor and the operation of his system can be beneficial and acquisition of such information is a possible reality. Since 9/11 the additional threat of terrorism has become more visible.
The final sentence in the scope/purpose statement is very important: it was recognized that the addition of just simple encryption of the protocols, for instance by adding “bump-in-the-wire” encryption boxes or even virtual private network (VPN) technologies would not be adequate for many situations. Security truly is an “end-to-end” requirement to ensure authenticated access to sensitive power system equipment, reliable and timely information on equipment functioning and failures, backup of critical systems, and audit capabilities that permit reconstruction of crucial events.
This work is to be published by the IEC as IEC 62351, Parts 1-7, titled:
· IEC 62351-1: Data and Communication Security – Introduction
· IEC 62351-2: Data and Communication Security – Glossary of Terms
·
IEC 62351-3: Data and Communication Security – Profiles
Including
·
IEC 62351-4: Data and Communication Security – Profiles
Including
· IEC 62351-5: Data and Communication Security – Security for IEC 60870-5 and Derivatives (i.e. DNP 3.0)
· IEC 62351-6: Data and Communication Security – Security for IEC 61850 Profiles
· IEC 62351-7: Data and Communication Security – Security Through Network and System Management
This first part of the standard covers the background on security for power system operations, and introductory information on the series of IEC 62351 security standards.
This part will include the definition of terms and acronyms used in the IEC 62351 standards. These definitions will be based on existing security and communications industry standard definitions as much as possible, given that security terms are widely used in other industries as well as in the power system industry.
Since it was formed, WG15 has undertaken the development of security standards for the four communication protocols listed above: IEC 60870-5, its derivative DNP, IEC 60870-6 (ICCP), and IEC 61850. These security standards must meet different security objectives for the different protocols, which vary depending upon how they are used. Some of the security standards can be used across a few of the protocols, while others are very specific to a particular profile. The different security objectives include authentication of entities through digital signatures, ensuring only authorized access, prevention of eavesdropping, prevention of playback and spoofing, and some degree of intrusion detection. For some profiles, all of these objectives are important; for others, only some are feasible given the computation constraints of certain field devices, the media speed constraints, the rapid response requirements for protective relaying, and the need to allow both secure and non-secured devices on the same network.
This work will be published by the IEC as IEC 62351, Parts 3-6, titled:
·
IEC 62351-3: Data and Communication Security –
Profiles Including
·
IEC 62351-4: Data and Communication Security –
Profiles Including
· IEC 62351-5: Data and Communication Security – Security for IEC 60870-5 and Derivatives (i.e. DNP 3.0) (these security standards cover both serial and networked profiles used by IEC 60870-5 and DNP)
·
IEC 62351-6: Data and Communication Security –
Security for IEC 61850 Peer-to-Peer Profiles (these security
standards cover those profiles in IEC 61850 that are not based on
The interrelationship of these security standards and the protocols are illustrated in Figure 10.

Figure 10: Interrelationship of IEC 62351 Security Standards and the TC57 Protocols
IEC 62351-3 provides security for any profile that
includes
Rather than re-inventing the wheel, it specifies the
use of
Specifically, IEC 62351-3 protects against
eavesdropping through
IEC 62351-4 provides security for profiles that
include the Manufacturing Message Specification (
It primarily works with
It also allows both secure and non-secure profiles to be used simultaneously, so that not all systems need to be upgraded with the security measures at the same time.
IEC 62351-5 provides different solutions for the serial version (primarily IEC 60870-5-101, as well as parts 102 and 103) and for the networked versions (IEC 60870-5-104 and DNP 3.0).
Specifically, the networked versions that run over
The serial version is usually used with
communications media that can only support low bit rates or with field
equipment that is compute-constrained. Therefore,
IEC 61850 contains three protocols that are
peer-to-peer multicast datagrams on a substation
WG15 has undertaken a fifth task in addition to these security standards for the SCADA protocols. Urged by TC57 to work toward end-to-end security, which entails a much larger scope than just the SCADA protocols. End-to-end security involves security policies, access control mechanisms, key management, audit logs, and other critical infrastructure protection issues.
WG15 decided to include network and system management of the Information Infrastructure under security. In essence, managing the Information Infrastructure is as crucial to the secure and reliable operation of the power system as any encryption or access management security schemes.
WG15 proposed to develop Management Information Base (MIBs) for the power system operational environment. These MIBs would reflect what information is needed to manage the information infrastructure as reliably as the power system infrastructure is managed. Once the Information Management requirements are defined, they can be structured as abstract objects, and formatted as standardized as Management Information Base (MIBs) to be compliant with information industry (i.e. IETF’s Simple Network Management Protocol - SNMP) standards. These MIBs are the Information Infrastructure equivalent to the 61850 object models of the Power System Infrastructure.

Figure 11: MIBs are the Information Infrastructure equivalent to the 61850 object models of the Power System Infrastructure
The Information Infrastructure in power operations is
not typically treated as a coherent infrastructure, but is viewed as a
collection of individual communication channels, separate databases,
multiple systems, and different protocols. Often SCADA systems perform some
minimal communications monitoring, such as whether communications are
available to their RTUs, and then they flag data as “unavailable” if
communications are lost. However, it is up to the maintenance personnel to
track down what the problem is, what equipment is affected, where the
equipment is located, and what should be done to fix the problem. All of
this is a lengthy and ad hoc process. In the mean time, the power system is
not being adequately monitored, and some control actions may be impossible.
As the analysis of the
Every utility is different in what information is
available to its maintenance staff. Telecommunication technicians are
generally responsible for tracking down any microwave or fiber cable
problems; telecommunication service providers must track their networks;
database administrators must determine if data is being retrieved correctly
from substation automation systems or from
In the future, the problem of information management will become increasingly complex. SCADA systems will no longer have exclusive control over the communications to the field, which may be provided by telecommunication providers, or by the corporate networks, or by other utilities. Intelligent Electronic Devices (IEDs) will have applications executing within them whose proper functioning is critical to power system reliability. Field devices will be communicating with other field devices, using channels not monitored by any SCADA system. Information networks in substations will rely on local “self-healing” procedures which will also not be explicitly monitored or controlled by today’s SCADA systems.
IEC 62351-7 is titled
Data and Communication Security –Management
Information Base (MIB) Requirements for End-to-End
Network Management. This part will define Management
Information Base (MIBs) that are specific for the power industry, to handle
network and system management through SNMP-based capabilities. These MIBs
will support communications network integrity, system and application
health, Intrusion Detection Systems (
The technology industry has developed two network management technologies: Simple Network Management Protocol (SNMP) for the Internet-based functions (standardized by the IETF), and Common Management Information Protocol (CMIP) as an ISO standard. In each of these technologies, Management Information Base (MIB) objects must be specified representing the state of different equipment, applications, and systems. Although some MIB objects are generic enough for typical network equipment to be used by the power industry, many specialized MIB objects will need to be developed to represent some of the very specialized equipment and special environments found in power system operations.
Examples of the network and system management requirements that the MIBs would fulfill include:
1. Communications Network Management: Monitoring the Networks and Protocols
a. Detecting network equipment permanent failures
b. Detecting network equipment temporary failures and/or resets
c. Detecting network equipment failovers to backup equipment or communication paths
d. Detecting the status of backup or spare equipment
e. Detecting communication protocol version and status
f. Detecting mis-matches of differing protocol versions and capabilities
g. Detecting tampered/malformed protocol messages
h. Detecting inadequately synchronized time clocks across networks
i. Detecting resource exhaustion forms of Denial of Service (DOS) attacks.
j. Detecting buffer overflow DOS attacks
k. Detecting physical access disruption
l. Detecting invalid network access
m. Detecting invalid application object access/operation
n. Ability to detect coordinated attacks across multiple systems
o. Collecting statistical information from network equipment
· Determining average message delivery times, slowest, fastest, etc.
· Counting number of messages, size of messages
p. Providing audit logs and records
2. Communications Network Management: Controlling the Networks
a. Manual issuing of on/off commands to network equipment
b. Manual issuing of switching commands to network equipment
c. Setting parameters and sequences for automated network actions
d. Automated actions in response to events, such as reconfiguration of the communications network upon equipment failure
3. System Management: Monitoring Intelligent Electronic Devices (IEDs)
a. Numbers and times of all stops and starts of systems, controllers, and applications
b. Status of each application and/or software module: stopped, suspended, running, not responding, inadequate or inconsistent input, errors in outputs, error state, etc.
c. Status of all network connections to an IED, including numbers and times of temporary and permanent failures
d. Status of any “keep-alive” heartbeats, including any missed heartbeats
e. Status of backup or failover mechanisms, such as numbers and times these mechanisms were unavailable
f. Status of data reporting: normal, not able to keep up with requests, missing data, etc.
g. Status of access: numbers, times, and types of unauthorized attempts to access data or issue controls
h. Anomalies in data access (e.g. individual request when normally reported periodically)
4. System Management: Control Actions within Intelligent Electronic Devices (IEDs)
a. Start or stop reporting
b. Restart IED
c. Kill and/or restart application
d. Re-establish connection to another IED
e. Shut down another IED
f. Provide event log of information events
g. Change password
h. Change backup or failover options
i. Providing audit logs and records
IEC TC57 WG15 has undertaken to develop recommendations for a comprehensive security process for power industry operations environments. This work will result in a Technical Report that recommends a reporting and security incident mitigation process that fulfils the needs of the power industry operations community and addresses specific issues related to the security of IEC TC57 protocols
This Technical Report would then be used by each country to determine the appropriate resource(s) and organizations to perform the recommended process for their country, with the understanding that inter-country coordination is required.
Work on this effort is just starting. The numbering of the resulting report has not been determined yet.
1. Parts 1, 3, 4, 5, and 6 were submitted as CDs last May. Comments from National Committees on the CDs were received and responded to during the last meeting of WG15 in September
2. Parts 3, 4, and 6 have been updated and have already been submitted for CDV (October 2005)
3. Part 1 is being updated, and will then be submitted for CDV (November 2005)
4. Part 5 is being updated. However, there is an outstanding issue that may delay its submittal as CDV, specifically the handling of derivatives to IEC 60870-5 (DNP3)
5. Part 2 (Glossary) will include only standardized terms. This work is still in progress
6. Part 7: This work is now moving forward, although no date for CD has yet been set.
7. Comprehensive security process: Work on this has just started.
Security measures should be built into every system from the moment they are conceived. Security includes not only the “encryption” that some people may assume is the only security measure necessary, but also authentication, role-based access control, prevention of denial of services, monitoring and audit functions for the information infrastructure, and last, but by no means least, security policies that enforce and supplement the security measures.